PII Scrubbing Workflow for Secure Call Recording Handling
Introduction and Overview
We have established a secure PII-scrubbing pipeline that automatically detects and redacts PII from call audio recordings and transcripts before any analysis is performed. This workflow ensures that all customer data is sanitized, protecting customer privacy and aligning with strict regulations (e.g., HIPAA, CFPB-related, PCI-DSS for payment data, and insurance industry standards).
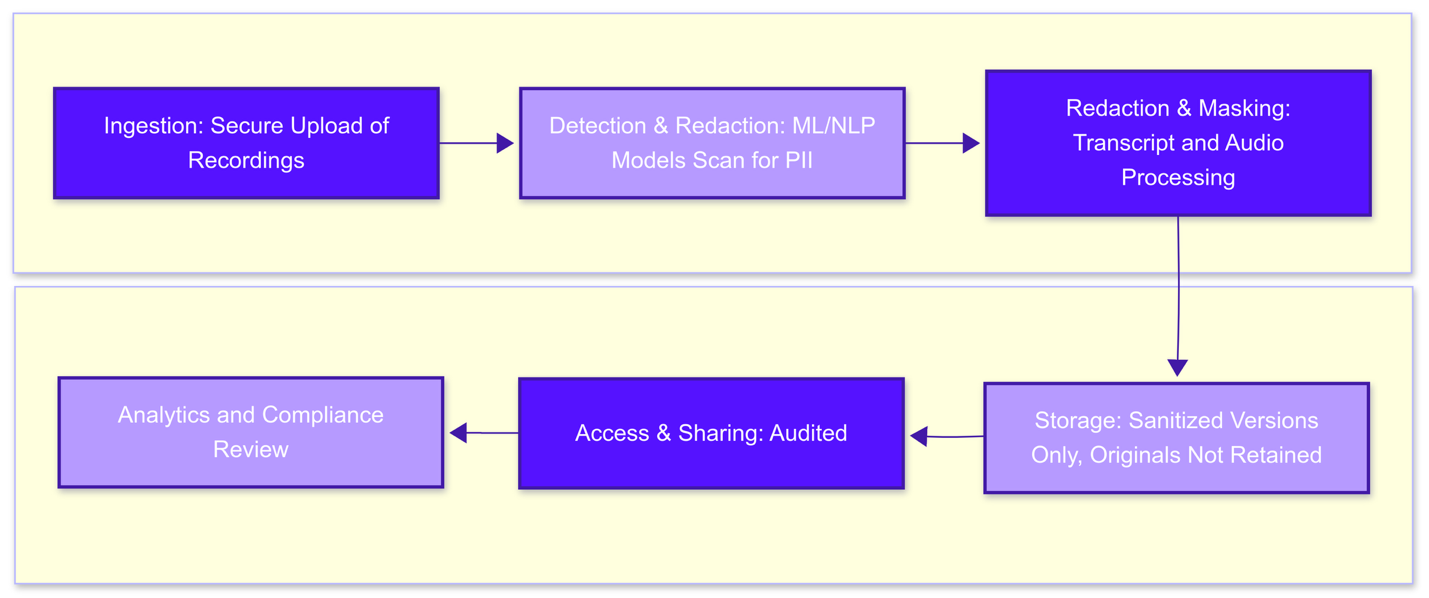
Our PII-scrubbing workflow has multiple stages, each with specific controls to ingest, detect, redact, store, and utilize call data in a secure and compliant manner. Advanced machine learning (ML) models are used to identify sensitive information in transcripts and audio, surpassing simple keyword matching. By incorporating AI, the system can detect PII in context (for example, distinguishing a numeric sequence as a credit card number or an address) more accurately than old rule-based methods. The following sections detail each stage of the pipeline and explain how it ensures that PII is scrubbed effectively while preserving the data's usefulness for analysis and training purposes.
Workflow Stages
- Ingestion: All customer call recordings are ingested through secure, encrypted channels as soon as they are created. They can be shared via app or secure messaging. If ingested via app, we enforce encryption in transit during upload (e.g. via SSL/TLS) to prevent any interception of sensitive data. The moment a new recording arrives, it triggers the scrubbing pipeline for immediate processing.
- Detection & Transcription: In this stage, the audio recording is converted to text using a speech-to-text engine (if a transcript is not already provided). The transcript enables easier scanning for PII. Our pipeline uses ML/NLP models to scan the transcript (and corresponding audio) for any PII indicators. The models are trained to detect a wide range of PII entity types, including:
- Personal identifiers Include Names, Social Security Numbers, dates of birth, phone numbers, email addresses, physical addresses, and other similar information.
- Financial information: Credit or debit card numbers, bank account details, routing numbers, card CVV codes, expiration dates, PINs.
- Health identifiers: Insurance policy numbers, medical record numbers, or other health-related personal info (to comply with HIPAA).
- Other PII: Any unique identifiers or sensitive data (account IDs, biometric identifiers, etc.) that should not be exposed.
Figure 1: PII Scrubbing Workflow
Each time a PII element is detected in the transcript, the system also notes the timestamp in the audio where that information was spoken. By having the start and end time of each sensitive snippet, we prepare for precise removal in both text and audio.
- Redaction & Masking: Once PII elements are identified, the pipeline redacts them in both the transcript and the audio:
- Transcript Redaction: In the text transcript, sensitive details are replaced with standardized placeholders (e.g. ****). The idea is to scrub the actual values while preserving the structure of the conversation.
- Audio Redaction: In the audio recording, the corresponding segments that contain PII are muted (silenced) or replaced with a harmless tone. Using the timestamps, the system knows exactly which portion of the waveform to suppress. We do not cut or delete the segment (which would alter the timing); instead, we programmatically mute the audio in those intervals. This ensures that the redacted audio retains the same length and conversational flow, with only the sensitive words rendered inaudible. For example, if a customer says, "My credit card number is 1234-5678-9012-3456," the audio file delivered after redaction will have silence (or a bleep sound) covering the part where the numbers are spoken. The rest of the conversation remains intact and uninterrupted, maintaining synchronization with the transcript.
By applying masking in both modalities, the transcript and audio stay synchronized – anyone listening to the call while reading the transcript will see placeholders at the same moments where the audio is muted.
- Storage of Sanitized Data: After redaction, only the sanitized versions of the data are retained in our systems. The original raw recordings (with PII) are never stored; they are discarded as soon as the scrubbing and verification process is complete. This “no original data” policy greatly limits our exposure. In effect, even if someone gained unauthorized access to our storage, they would only find anonymized call records with no sensitive personal info present. The sanitized transcripts and redacted audio files are stored in secure storage with strong encryption at rest. In line with industry best practices, all call records and associated data are encrypted on disk using robust encryption (such as AES-256). For example, CallRail’s system ensures all call recordings and transcripts are fully encrypted at rest, protecting the data even if storage media are stolen or compromised.
Additionally, any metadata or logs we keep (for example, the fact that a redaction occurred at a certain time) are also treated as sensitive and protected. By not keeping the original unsanitized data, we drastically reduce the risk surface: there is no trove of raw PII-laden recordings to worry about. Everything in our database is scrubbed and compliant.
- Audit Trails: Every access or action taken on the call records is logged. This includes who accessed a file or transcript, when, and what they did (viewed, played audio, shared, etc.). These audit trails are critical for compliance and security oversight. They ensure accountability; if someone were to attempt improper use of data, we could detect it and trace it. Audit logs are routinely reviewed as part of our security protocols, and they also provide evidence during compliance audits that our data is handled appropriately. In essence, any interaction with the scrubbed data is transparently recorded.
5. Analytics and Utilization (Post-Scrubbing): Once the data has been sanitized, it can be safely used for various beneficial purposes within the organization:
- Coaching and Training: Supervisors and training personnel use the redacted call recordings and transcripts to coach agents. They can highlight good practices or areas for improvement by referencing actual call scenarios, without any risk of leaking a customer's personal details. Even if calls are played in a training session or stored in a library of examples, all the personal data has been removed or masked. This allows realistic training while maintaining privacy.
- Quality Assurance and Compliance Review: The compliance team can review calls to ensure agents follow proper procedures and scripts (for example, verifying that agents are not asking for unnecessary information or that required disclosures are given). Since the recordings are scrubbed, the compliance officers can focus on agent behavior and compliance without encountering raw customer PII. If needed, the system’s audit logs and redaction logs can be reviewed to confirm that no sensitive info was retained. This helps demonstrate regulatory compliance. In regulated sectors like healthcare and finance, audit-friendly data access is vital. Our redaction process preserves the integrity of call records for audits while removing sensitive information, allowing us to demonstrate what happened on the call without exposing private details.
- Analytics and Reporting: Sanitized transcripts can be fed into analytics tools to derive business intelligence. For example, we can perform sentiment analysis, identify common customer pain points, measure call durations and outcomes, and so on, across thousands of calls. Since all PII has been removed, this analysis does not pose a risk of privacy breaches. Companies gain insights into customer needs and operational performance while staying fully compliant with privacy laws. Trends can be reported (e.g., the frequency of certain complaints or keywords) without ever reporting a specific person's data. In summary, the data remains useful for decision-making purposes, but poses no harm from a privacy standpoint.
By the end of this pipeline, we have transformed raw call data into a PII-sanitized dataset that is secure and compliant, ready for use in improving our services.
Compliance Alignment
Our PII-scrubbing workflow is designed with compliance in mind from the ground up. It adheres to or exceeds the requirements of major data privacy and security regulations relevant to call recordings:
- HIPAA (Health Insurance Portability and Accountability Act): For clients in the healthcare or insurance sectors who handle patient information, our process ensures that Protected Health Information (PHI) is safeguarded. HIPAA mandates strict protection of any patient-identifiable information. In our pipeline, any health identifiers or medical information mentioned in calls (e.g., policy numbers, medical conditions, prescription details) are detected and redacted. By removing or masking patient names and health details in recordings, we help healthcare providers maintain HIPAA compliance and protect patient confidentiality. Moreover, by not storing the original call with PHI and by controlling access to the sanitized data, we eliminate potential points of failure. Our encryption and access controls further ensure that even if data is intercepted or improperly accessed, it remains unintelligible and secure.
- CFPB and PCI-DSS (Payment Card Industry Data Security Standard): For any business that handles credit card information over the phone (e.g., taking payments by phone), PCI-DSS compliance is essential. This standard requires that sensitive cardholder data (like credit card numbers, expiration dates, CVV codes) not be stored unless necessary, and if stored, it must be heavily protected. Our scrubbing workflow removes credit card numbers and other payment details from call records, thus preventing the storage of this sensitive financial data. For instance, if a customer reads out their credit card number during a call, that number will be stripped out of the transcript and muted in the audio, so the recorded data never retains the actual card number. By doing so, we dramatically reduce PCI scope. The remaining sanitized call data can be stored without triggering the strict handling requirements that raw credit card data would. In effect, our system aligns with PCI-DSS by “masking sensitive payment data in recorded interactions”, allowing transactions to be handled securely without exposing the card details in stored recordings. This protects both the customer (their card info can’t be stolen from a call record that no longer has it) and us (from liability and compliance violations).
- Insurance Industry Standards: Insurance companies handle a wealth of personal data – not only health information (if health insurance is involved) but also personal details for underwriting policies, claims information, and sometimes financial information. While there may not be a single monolithic law for all insurance data globally, insurers must adhere to general data protection principles and often specific regulations (for example, state privacy laws, regulations from bodies like the NAIC, or even GDPR/CCPA if applicable to their customer base). Our PII scrubbing process supports these needs by enforcing stringent privacy controls on all personal data in call recordings. That includes policy numbers, claim details, addresses, birth dates, driver’s license numbers, and any other PII shared during calls. By redacting such details, we align with the data minimization and protection principles common in insurance regulations. In short, we treat insurance customer data with the same high level of care as health or financial data. The result is a significantly lower risk of data breaches or privacy violations, which helps our clients in the insurance industry maintain trust and comply with their legal obligations. Our approach of only sharing scrubbed call data for business use means that even if multiple departments (claims, underwriting, customer service, etc.) use the call recordings, none of them receive unnecessary personal information that could lead to misuse or errors.
In addition to the above, our practices inherently support compliance with broader privacy laws and frameworks: - We effectively implement principles of GDPR/CCPA by only keeping de-identified data (which is generally outside the scope of personal data regulations). If a user ever exercises rights, such as a data deletion request, there would be no raw PII in their call records to delete – only anonymized data remains. - We meet or exceed the requirements of data protection standards by using encryption, access control, and monitoring (which are often explicitly required by laws or expected by regulators).
Regular compliance audits are conducted on our processes to verify that the scrubbing works as intended and that no sensitive data is slipping through. We document all measures and can provide compliance reports or certifications as needed to our clients. By aligning our workflow with these regulations, we not only avoid legal penalties but also demonstrate our commitment to protecting customer privacy.
Security Measures and Data Protection Controls
Beyond just removing PII, our pipeline incorporates multiple security measures to protect the data at every stage. These measures ensure that the system itself is robust against unauthorized access or data leakage, complementing the redaction process:
- Encryption in Transit and At Rest: All data is encrypted both in transit and at rest, as a fundamental security practice. Encryption in transit means that when recordings and transcripts are transferred between services or downloaded, they are sent over encrypted connections (SSL/TLS), thereby preventing eavesdropping. Encryption at rest refers to the process of storing data on our servers or databases in an encrypted format. This way, even if someone were to access the storage media, they would be unable to read the data without the proper decryption keys. For example, CallRail notes that all call records and related data are fully encrypted when stored on disk, and only decrypted when accessed by authorized users. Similarly, our system utilizes strong encryption key management – whether with cloud providers or on-premise solutions – to secure the stored call information. These encryption measures are critical for compliance (many regulations explicitly require encryption for sensitive data) and for overall risk mitigation.
- Audit Logging and Monitoring: Every interaction with the system is logged. We maintain detailed logs of who accessed data, when, what actions were taken (view, edit, share, delete), and from where. These logs cannot be altered by end users and are stored securely. We also monitor these logs for unusual access patterns. For example, if an account that normally only accesses a few transcripts suddenly attempts to download hundreds of audio files, our security team would be alerted to investigate the issue. Audit logs serve a dual purpose: security monitoring (detecting potential misuse or breaches) and compliance evidence (demonstrating to regulators or clients that data access is well-governed). Our commitment to full audit logging provides transparency and accountability for all data handling actions.
- Regular Compliance Audits and Reviews: We don’t just set up the system and forget it – we conduct regular reviews to ensure ongoing compliance. This includes internal audits of scrubbing accuracy (to ensure the ML models correctly capture all PII and that no new types of sensitive data are overlooked), reviews of access logs, and periodic reviews of access rights (to remove or adjust any permissions that are no longer necessary). We also stay updated with changes in regulations. For instance, if new laws or industry guidelines emerge defining new categories of sensitive information, we update our detection models and processes accordingly. Our infrastructure and policies are also subject to external audits or certifications when required (for example, if a client requires a SOC 2 audit or a similar assessment, our practices, such as this scrubbing pipeline, would be part of the scope). The idea is to maintain a “trust but verify” stance – we trust our controls, but we also verify them regularly through audits and tests.
- Secure Architecture and Scalability: The pipeline is built on a secure architecture (leveraging proven cloud services and secure coding practices) that is also scalable. All components that handle the data (such as the transcription engine, the ML detection models, and the storage) operate in a secure environment with network security controls (like VPC isolation, firewalls, etc.). The pipeline can scale to handle large volumes of calls by leveraging cloud infrastructure, meaning that as call volume grows, we can maintain the same level of scrubbing without performance issues. The scalability is important not only for performance but also for future-proofing: our solution can adapt to different industries and increasing data needs without compromising security. We can also incorporate new PII detection requirements as needed (for example, if we expand to international operations, we can include detection for things like national ID numbers of other countries, etc., thanks to the customizable AI models).
In summary, our security measures ensure that from the moment a call is recorded to the moment the sanitized data is used for analysis, multiple layers of protection are in place. Data is encrypted, access is restricted, actions are logged, and the process is regularly verified. This comprehensive approach significantly reduces the risk of sensitive information leaking. It provides confidence to all stakeholders (our company, our clients, and the customers whose calls are recorded) that the data is handled with utmost care and discretion.
Conclusion
Through the above stages and measures, we have implemented a comprehensive PII-scrubbing pipeline that secures customer call recordings from end to end. Every recording is immediately processed by an automated engine that detects and redacts sensitive personal information from both the audio and transcript, ensuring that no unprotected PII ever persists in our systems. The scrubbed data is encrypted, access-controlled, and fully compliant with regulations like HIPAA for health data, PCI-DSS for payment data, and relevant insurance and privacy standards. We maintain thorough audit trails and conduct regular compliance audits to verify the effectiveness of our processes. This pipeline not only ensures compliance with regulations but also demonstrates our commitment to customer privacy and data security.